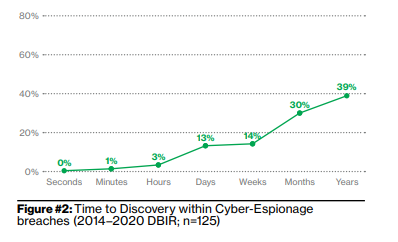
The 2020 Cyber-Espionage Report pulls seven years of data to determine threat actors, motives and actions | 2020-11-18 | Security Magazine

China Accuses NSA of Cyber Espionage in Repeated Breaches of Xi'an Research University - CPO Magazine


![How to Detect and Prevent Industrial Espionage [with Examples] | Ekran System How to Detect and Prevent Industrial Espionage [with Examples] | Ekran System](https://www.ekransystem.com/sites/default/files/how_to_detect_and_prevent_industrial_espionage/figure4.jpg)










![How to Detect and Prevent Industrial Espionage [with Examples] | Ekran System How to Detect and Prevent Industrial Espionage [with Examples] | Ekran System](https://www.ekransystem.com/sites/default/files/how_to_detect_and_prevent_industrial_espionage/figure5.jpg)


![How to Detect and Prevent Industrial Espionage [with Examples] | Ekran System How to Detect and Prevent Industrial Espionage [with Examples] | Ekran System](https://www.ekransystem.com/sites/default/files/how_to_detect_and_prevent_industrial_espionage/figure3.jpg)

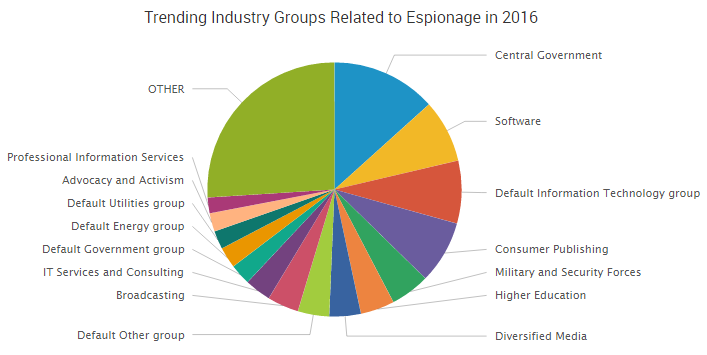




/https://cyware-ent.s3.amazonaws.com/image_bank/3644_APT42-Rasomware-Thumbnail-3.png)
![How to Detect and Prevent Industrial Espionage [with Examples] | Ekran System How to Detect and Prevent Industrial Espionage [with Examples] | Ekran System](https://www.ekransystem.com/sites/default/files/how_to_detect_and_prevent_industrial_espionage/figure1.jpg)