Tanium Threat Response + Google Chronicle | Enterprise-class Unified Endpoint Security (UES) paired with massively scalable, cloud-native security analytics. This video shows how to use a... | By M-Security Tech Philippines Inc.
Free Automated Malware Analysis Service - powered by Falcon Sandbox - Viewing online file analysis results for 'EFRService.exe'
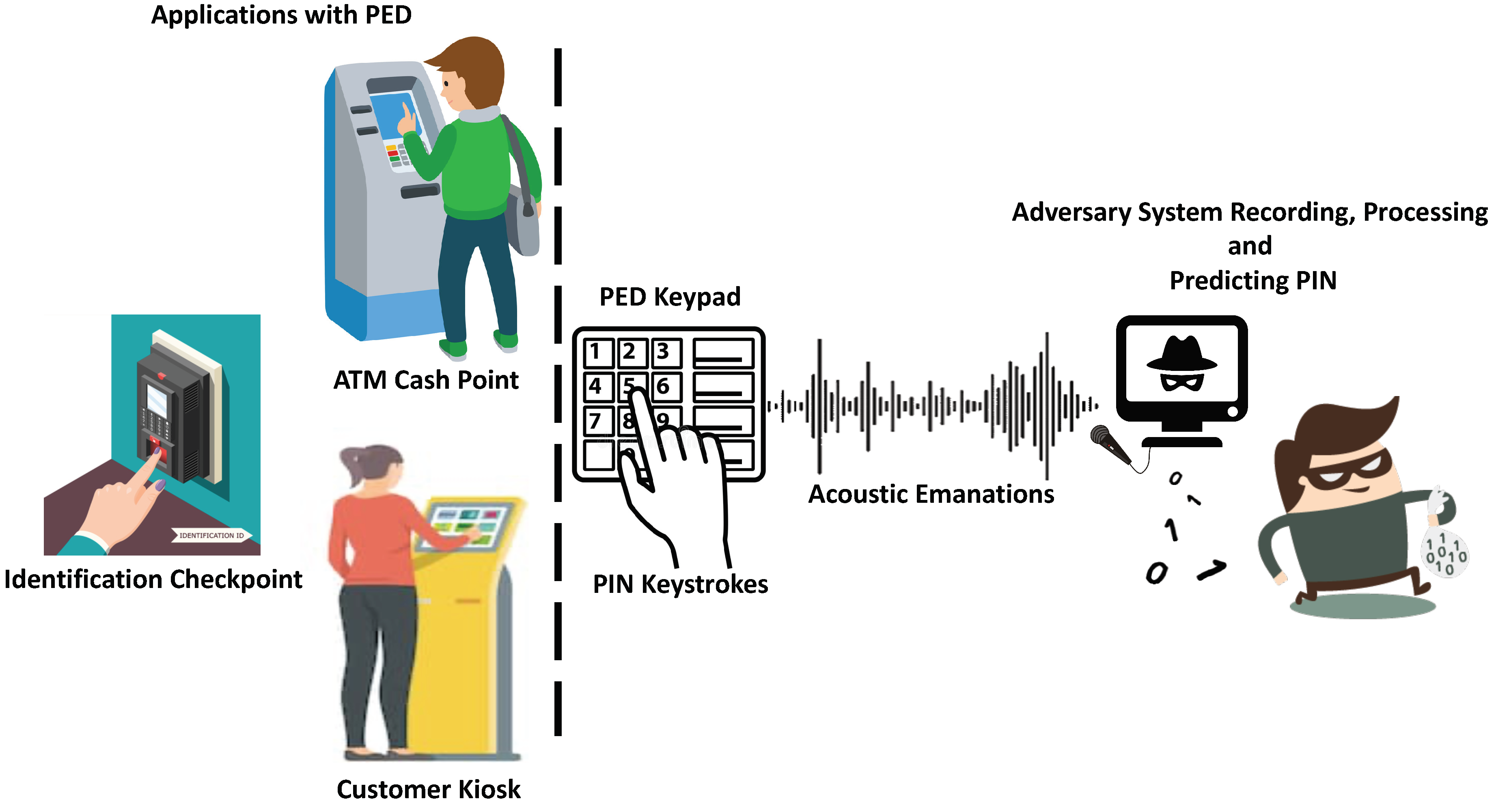
Sensors | Free Full-Text | Behavioral Acoustic Emanations: Attack and Verification of PIN Entry Using Keypress Sounds


.jpg?width=1000&name=Panda%20Adaptive%20Defense%20360(USE).jpg)
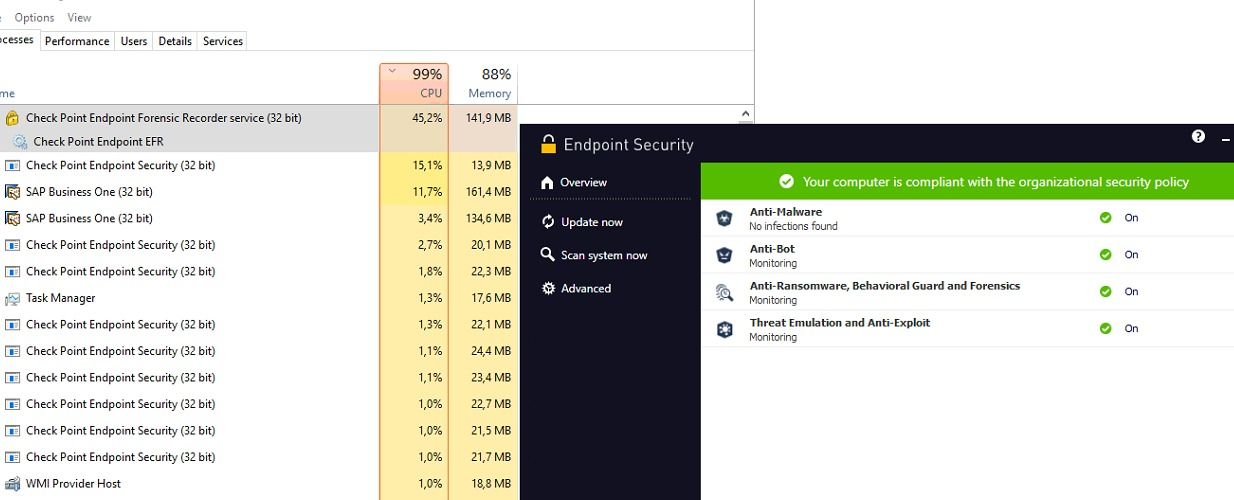
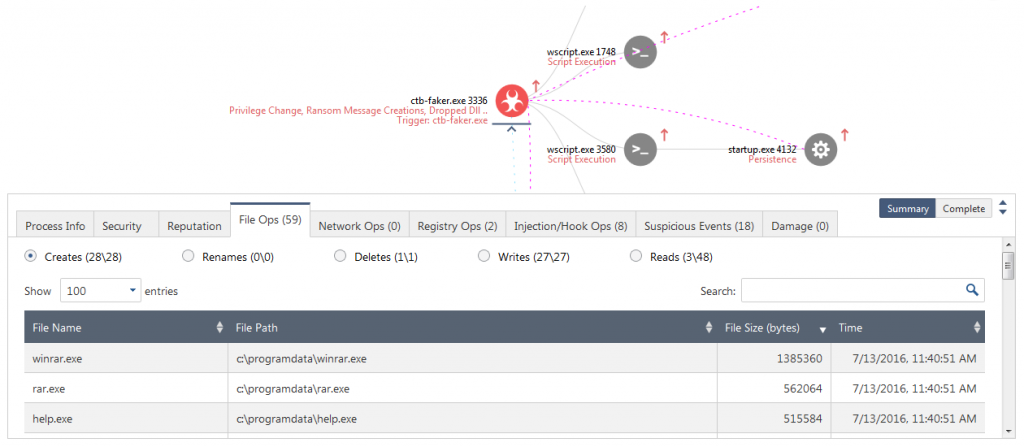
.jpg?width=1000&name=Cytomic_EDR(USE).jpg)

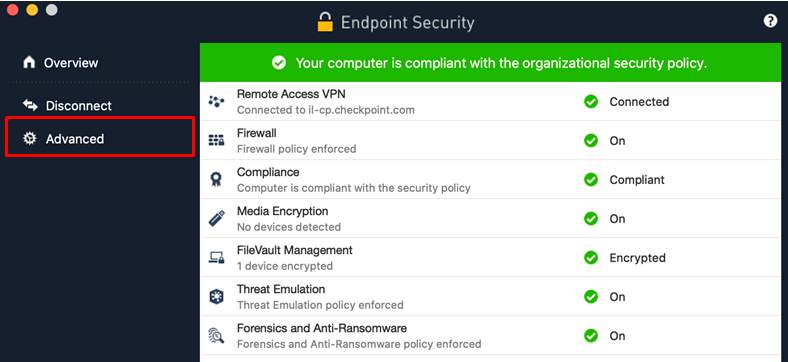
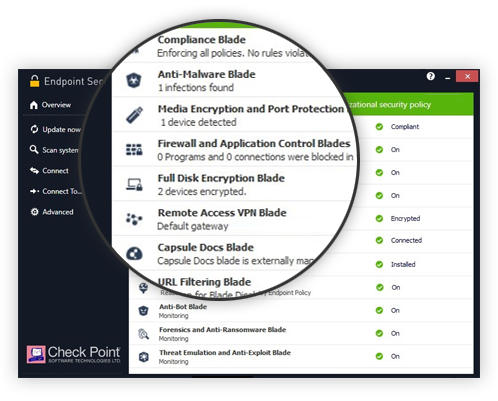
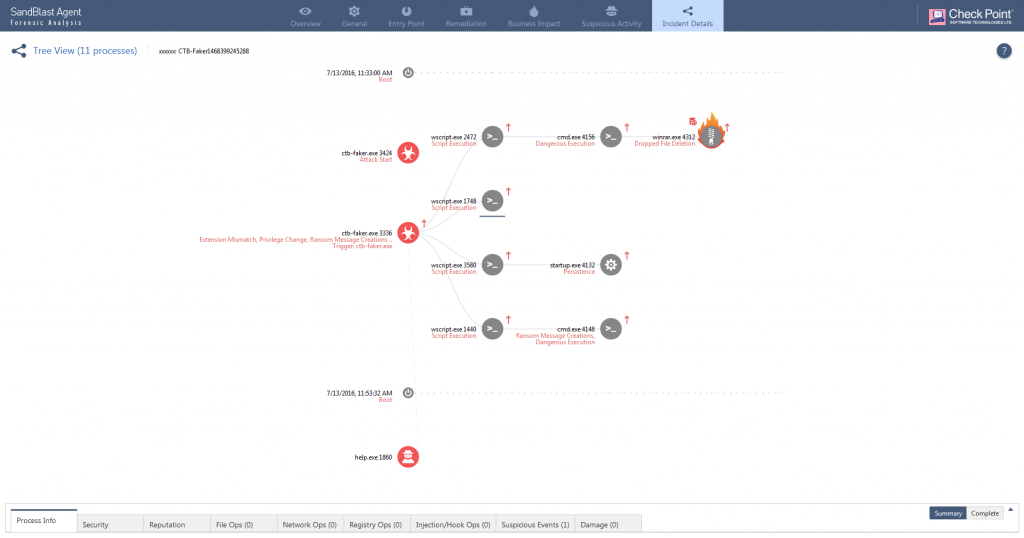
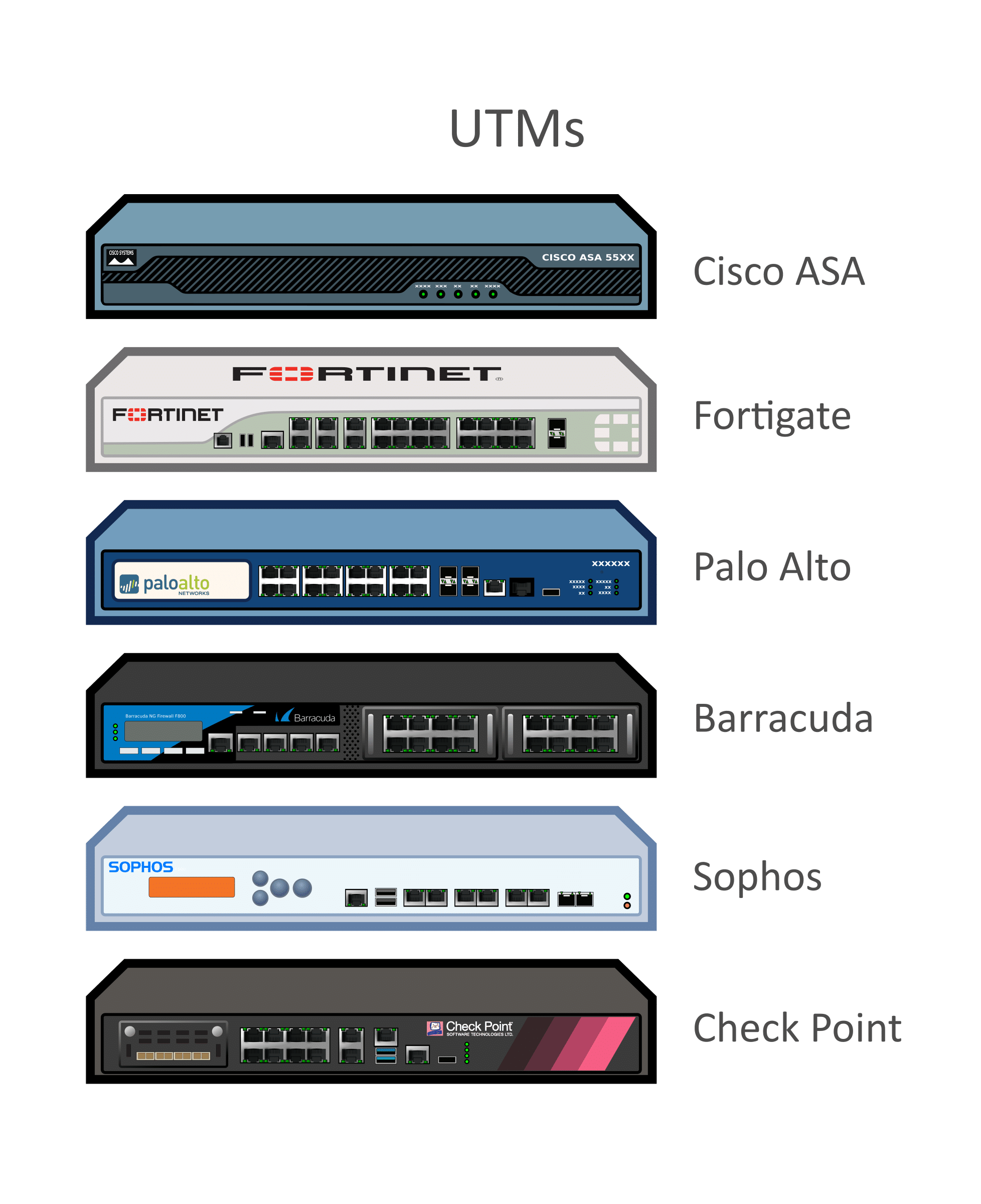
.jpg?width=1000&name=Check%20Point%20Harmony%20EDR%20(USE).jpg)
.jpg?width=1000&name=Malwarebytes_EDR(USE).jpg)